With v3.12.1 we added some optimizations and fixed several bugs.
For even more features and optimizations (see the comparision page), please use the integrated pro upgrader to start a free 30-day-trial of Maps Marker Pro.
Pro v3.1 has also been released today with the following highlights:
An update to the latest version is – as always – highly recommended.
Let me know what you think about this new release by submitting a review!
If you want to keep up to date with the latest Maps Marker development, please follow @MapsMarker on twitter (= most current updates), on Facebook, Google+ or subscribe to news via RSS or via RSS/email.
We would also like to invite you to join our affiliate program which offers commissions up to 50%. If you are interested in becoming a reseller, please visit https://www.mapsmarker.com/reseller
Now let´s get to the highlights of free v3.12.1:
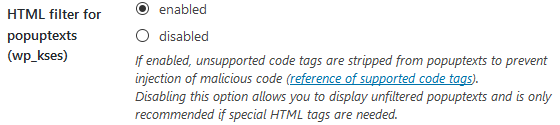
By default, popuptexts are now filtered using wp_kses() which is also used for default WordPress content like posts and pages.
As a result, only allowed HTML element names, attribute names and attribute values plus only sane HTML entities will be displayed – JavaScript code (which could be used for Cross site scripting – XSS for example) is stripped from output.
If you need unfiltered popuptexts to e.g. execute custom Javascript code, you can disable this option at Settings / Misc / Compatibility settings:
No technology is perfect, and neither is ours. There will always be things that we can have overlooked. While we can’t avoid having blind spots, we can do something to identify them: We’re calling out to security researchers everywhere to help us find security bugs and security issues in our products.

Photo: Boba Fett cosplayer at the 2012 Phoenix Comicon in Phoenix, Arizona. Author: Gage Skidmore (own work) [CC-BY SA 2.0] via Wikimedia Commons]
Join the ranks of Boba Fett, Greedo & Co.: Become a bounty hunter for Maps Marker Pro
We offer a $ 10 bounty for valid security bugs (for example simple XSS), with the option for larger bounties for more serious bugs, like for example remote code execution exploits, SQL injection or privilege escalation. In addition, we offer a professional package for Maps Marker Pro that’s valid for 25 domains, including access to updates and support for 3 years (list price: € 499) for each person reporting a valid security bug.
Bounties are paid for source code vulnerabilities, but feel to submit vulnerabilities outside that for an optional smaller bounty. We’ve advertised our bounty hunt on the bug bounty platform HackerOne, where you’ll find a full description of our rewards program with a list of valid targets: https://hackerone.com/mapsmarker_com_e_u
Are you a professional WordPress developer who knows the ins and outs of Maps Marker Pro? Great! Get in touch, and maybe we can recommend you to customers who want individual customizations or custom developments based on one of our Maps Marker Pro APIs.

Sometimes, you just need a custom made product – and someone you can trust to create it for you.
Photo by Fancycrave [CC0 Public Domain] via pexels.com
We’re working hard on delivering the best mapping solution for everyone. But from time to time, clients want their own special things: Individual customizations of Maps Marker Pro, hand-crafted to fit their unique business case, in many cases involving one of our Maps Marker Pro APIs. In this case, we like to refer them to our trusted network of experts.
If you are
then please send us an email, containing a short introduction of yourself, your skills and experience as well as links to previous works.
If we’re a good fit for each other, we will happily add you to our network and, if something comes up, we will recommend you to customers who’s needs for customizations match with your skills.
We do not want to take any commission – our gain is the happiness of our customers, when we can refer them to someone they can rely on for their further needs.
We’re looking forward to hearing from you!
Since the start of our security bug bounty program on May 19th we have received several vulnerability reports – due to our attention on secure coding and 3 penetration tests in the last 4 years no severe or critical issues were found though. All but the first issue from the list below could only have been exploited by users with backend access – and in most cases with admin users only.
Some additional thoughts why those vulnerabilities were not detected by us so far, although we are doing regular security checks: the attack vector of an admin who e.g. inject malicious code into Leaflet Maps Marker settings was not completely covered by us so far, as such an attacker would have had direct access to theme or plugin files – making it much easier to e.g. inject malicious code or change database tables directly than to use Leaflet Maps Marker for Cross site scripting.
Nevertheless although the exploitability of the reported vulnerabilities is low, we take those reports seriously and fixed all of them respectively hardened our entire codebase to prevent future similar vulnerabilities.
Thanks to many motivated contributors, this release includes the following updated translations:
If you want to contribute to translations (new Hindi translators would be appreciated!), please visit https://translate.mapsmarker.com/projects/lmm for more information.
Please note that translators are also compensated for their contribution – for example if a translation is finished less than 80%, the translator receives a free 25 licenses pack worth €249 as a compensation for completing the translation to 100%.
We are currently working on a relaunch of our website www.mapsmarker.com which will also feature an updated knowledge base and documentation.
Please understand that we are not able to promise any release dates for new features. We are dynamically aligning our roadmap based on feedback from our users. Anyway we keep the flexibility to add optimizations and bugfixes with rather unplanned minor releases resulting mostly from users feedback.
Please subscribe to this blog (via RSS or Email) or follow @MapsMarker on twitter (= most current updates) if you want to stay up to date with the latest development news.
| optimized performance for Google basemaps by enabling GoogleMutant Javascript library for all users | |
| new widget “show latest marker map” | |
| global basemap setting “nowrap”: (if set to true, tiles will not load outside the world width instead of repeating, default: false) | |
| list all markers page enhancement: dropdown added to filter markers by layer | |
| loading indicator for GeoJSON download and marker clustering | |
| Bounty Hunters wanted! Find security bugs to earn cash and licenses – click here for more details | |
| compatibility check for “WP Super Cache” debug output which can cause layer maps to break | |
| compatibility check for Admin Custom Login which causes the navigation on the settings page to break | |
| compatibility check for Fast Velocity Minify plugin | |
| option “HTML filter for popuptexts” to prevent injection of malicious code – enabled by default (thx jackl via hackerone) | |
| compatibility check for theme Divi 3+ which can cause maps to break if option “Where to include Javascript files?” is set to footer | |
| Looking for developers to recommend to our clients for customizations – more details at mapsmarker.com/network | |
| Autoptimize plugin compatibility check: also verify if option “Also aggregate inline JS?” is set (which is causing maps to break) | |
| use wp_kses() instead of strip_tags() for recent marker widget to support selected HTML elements | |
| only dequeue Google Maps API scripts added by other plugins instead of deregistering them if related option is enabled (as this could break dependend scripts & plugins like WP GPX maps) | |
| prevent duplicate markers when exporting markers from multi-layer-maps to KML, GeoRSS & Wikitude (thx Eric & Thorsten!) | |
| fix PHP APC cache detection for importer | |
| XLS export for marker and layer maps was broken if PHP 7.1+ is used | |
| markers and layers could not be saved on iOS devices due to a bug in Safari´s datetime-local implementation (thx Natalia!) | |
| window width on marker and layer edit pages could not be fully utilized on iOS devices (thx Natalia!) | |
| list of markers was not fully responsive if images larger than 440px in popuptexts were used (thx Georges!) | |
| Low impact: stored XSS vulnerability for QR code image size (only if Google is set as default QR code provider – thx whitesector via hackerone) | |
| Low impact: XSS vulnerabilities on marker & layer edit pages (thx to victemz & 0xnop via hackerone) | |
| Low impact: command injection vulnerability in marker & layer export files (thx to kiranreddy via hackerone) | |
| Low impact: stored XSS vulnerability for createdby and updatedby fields on backend | |
| Low impact: stored XSS vulnerability on tools page only if Webapi is enabled (thx whitesector via hackerone) | |
| Low impact: stored XSS vulnerability for custom default marker icon (thx whitesector via hackerone) | |
| Translation updates In case you want to help with translations, please visit the web-based translation plattform |
|
| updated Catalan translation thanks to Efraim Bayarri, Vicent Cubells, http://vcubells.net and Marta Espinalt, http://www.martika.es | |
| updated Chinese translation thanks to John Shen, http://www.synyan.net and ck | |
| updated German translation | |
| updated Indonesian translation thanks to Andy Aditya Sastrawikarta and Emir Hartato, http://whateverisaid.wordpress.com and Phibu Reza, http://www.dedoho.pw/ | |
| updated Italian translation thanks to Luca Barbetti, http://twitter.com/okibone and Angelo Giammarresi – http://www.wocmultimedia.biz | |
| updated Japanese translations thanks to Shu Higash and Taisuke Shimamoto | |
| updated Lithuanian translation thanks to Donatas Liaudaitis – http://www.transleta.co.uk and Ovidijus – http://www.manokarkle.lt | |
| updated Russian translation thanks to Ekaterina Golubina (supported by Teplitsa of Social Technologies – http://te-st.ru) and Vyacheslav Strenadko, http://slavblog.ru | |
| updated Spanish translation thanks to David Ramírez, http://www.hiperterminal.com, Alvaro Lara, http://www.alvarolara.com, Victor Guevara, http://1sistemas.net, Ricardo Viteri, http://www.labviteri.com, Juan Valdes and Marta Espinalt, http://www.martika.es | |
| updated Swedish translation thanks to Olof Odier, Tedy Warsitha, Dan Paulsson http://www.paulsson.eu, Elger Lindgren, http://bilddigital.se, Anton Andreasson, http://andreasson.org/ and Tony Lygnersjö – https://www.dumsnal.se/ | |
How to download / update
The easiest way to update is to use the WordPress update process: login with an user who has admin privileges, navigate to Dashboard / Updates, select plugins to update and press the button “Update Plugins”. Alternatively you can also download the current version here, unzip the package and overwrite the plugin´s files on your webserver.